In today’s digital age, businesses face an ever-evolving landscape of cyber threats, from data breaches to ransomware attacks. As technology advances, so do the tactics of hackers, making it crucial for companies to prioritize cybersecurity. Effective cybersecurity solutions can protect your business from financial loss, reputational damage, and compromised customer data. By implementing robust security measures, you can safeguard your organization’s digital assets and ensure the continuity of your operations, giving you peace of mind and a competitive edge in the market, and allowing you to focus on growth and innovation. Strong security is essential.
Introduction to Cybersecurity Solutions As a business owner, it is essential to protect your company from digital threats. Cybersecurity solutions are designed to safeguard your business from various types of cyber attacks, including malware, phishing, and ransomware. In this guide, we will explore the importance of cybersecurity solutions and provide you with the information you need to protect your business.
Understanding the Importance of Cybersecurity
Understanding the importance of cybersecurity is crucial for businesses of all sizes. Cybersecurity is the practice of protecting computer systems, networks, and sensitive data from unauthorized access, use, disclosure, disruption, modification, or destruction. This is achieved through the use of security protocols, firewalls, and encryption. By implementing effective cybersecurity measures, businesses can prevent data breaches, financial losses, and reputational damage.
Types of Cybersecurity Solutions
There are several types of cybersecurity solutions available, including network security, endpoint security, application security, and cloud security. Network security solutions protect your business’s network infrastructure from intrusions and attacks. Endpoint security solutions protect devices such as laptops, smartphones, and tablets from malware and other threats. Application security solutions protect software applications from vulnerabilities and exploits. Cloud security solutions protect your business’s cloud infrastructure from unauthorized access and data breaches.
Benefits of Implementing Cybersecurity Solutions
Implementing cybersecurity solutions can bring numerous benefits to your business, including Improved security, Increased efficiency, and Enhanced reputation. By protecting your business from cyber threats, you can prevent financial losses and reputational damage. Additionally, cybersecurity solutions can help you comply with regulatory requirements and industry standards. The following table highlights the benefits of implementing cybersecurity solutions:
| Benefit | Description |
|---|---|
| Improved Security | Protection from cyber threats and data breaches |
| Increased Efficiency | Streamlined security protocols and incident response |
| Enhanced Reputation | Protection of customer data and business reputation |
Best Practices for Implementing Cybersecurity Solutions
Implementing cybersecurity solutions requires careful planning and execution. Best practices include conducting regular security audits, implementing strong passwords, and providing employee training. Additionally, businesses should stay up-to-date with the latest security patches and vulnerability fixes. By following these best practices, businesses can ensure that their cybersecurity solutions are effective and aligned with their business goals.
Future of Cybersecurity Solutions
The future of cybersecurity solutions is evolving rapidly, with new technologies and threats emerging every day. Artificial intelligence, machine learning, and cloud computing are changing the way businesses approach cybersecurity. As cyber threats become more sophisticated, businesses must stay ahead of the curve by investing in innovative cybersecurity solutions and staying informed about the latest security trends. By doing so, businesses can protect themselves from emerging threats and stay ahead of the competition.
How does cybersecurity protect businesses?
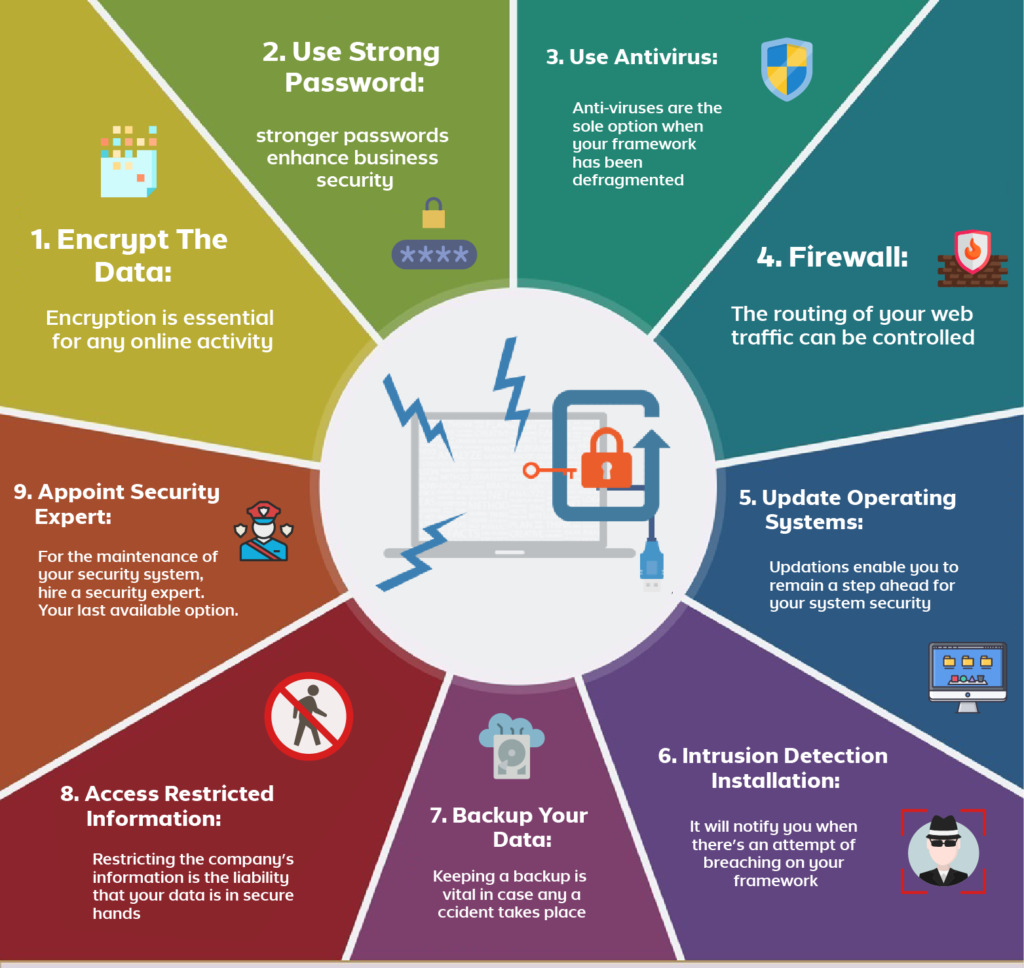
Cybersecurity plays a vital role in protecting businesses from various types of cyber threats. It helps to prevent unauthorized access to sensitive data, protects against malware and viruses, and ensures the integrity of business operations. A robust cybersecurity system enables businesses to detect and respond to security incidents in a timely manner, minimizing the impact of a breach. This is achieved through a combination of technological and procedural measures, including firewalls, encryption, access controls, and incident response plans.
Protecting Business Data
Cybersecurity is essential for protecting business data from unauthorized access and theft. Businesses handle sensitive information, including customer data, financial information, and intellectual property. A data breach can result in significant financial losses and damage to a company’s reputation. To protect business data, cybersecurity measures such as encryption, access controls, and data backups are implemented. These measures ensure that sensitive data is securely stored and transmitted, and that unauthorized access is prevented. Some key measures to protect business data include:
- Implementing strong passwords and multi-factor authentication to prevent unauthorized access
- Using encryption to protect data both in transit and at rest
- Conducting regular data backups to ensure business continuity in the event of a data loss
Preventing Cyber Attacks
Cybersecurity helps to prevent cyber attacks by detecting and blocking malicious traffic. Businesses are vulnerable to various types of cyber attacks, including phishing, ransomware, and distributed denial-of-service (DDoS) attacks. A robust cybersecurity system includes firewalls, intrusion detection systems, and anti-virus software to detect and block malicious activity. Additionally, employee education and awareness programs are crucial in preventing cyber attacks, as employees are often the weakest link in a company’s security chain. Some key measures to prevent cyber attacks include:
- Implementing firewalls and intrusion detection systems to detect and block malicious traffic
- Using anti-virus software and keeping operating systems and software up to date
- Conducting regular security audits and penetration testing to identify and address vulnerabilities
Ensuring Business Continuity
Cybersecurity is essential for ensuring business continuity in the event of a security incident. A cyber attack or data breach can result in significant disruptions to business operations, resulting in lost revenue and damage to a company’s reputation. A robust cybersecurity system includes incident response plans and business continuity plans to ensure that business operations can quickly recover in the event of a security incident. This includes identifying and prioritizing critical business processes, developing alternative processes, and conducting regular disaster recovery exercises. Some key measures to ensure business continuity include:
- Developing incident response plans and business continuity plans to ensure quick recovery
- Identifying and prioritizing critical business processes and developing alternative processes
- Conducting regular disaster recovery exercises to test business continuity plans
What are the solutions for cyber security threats?
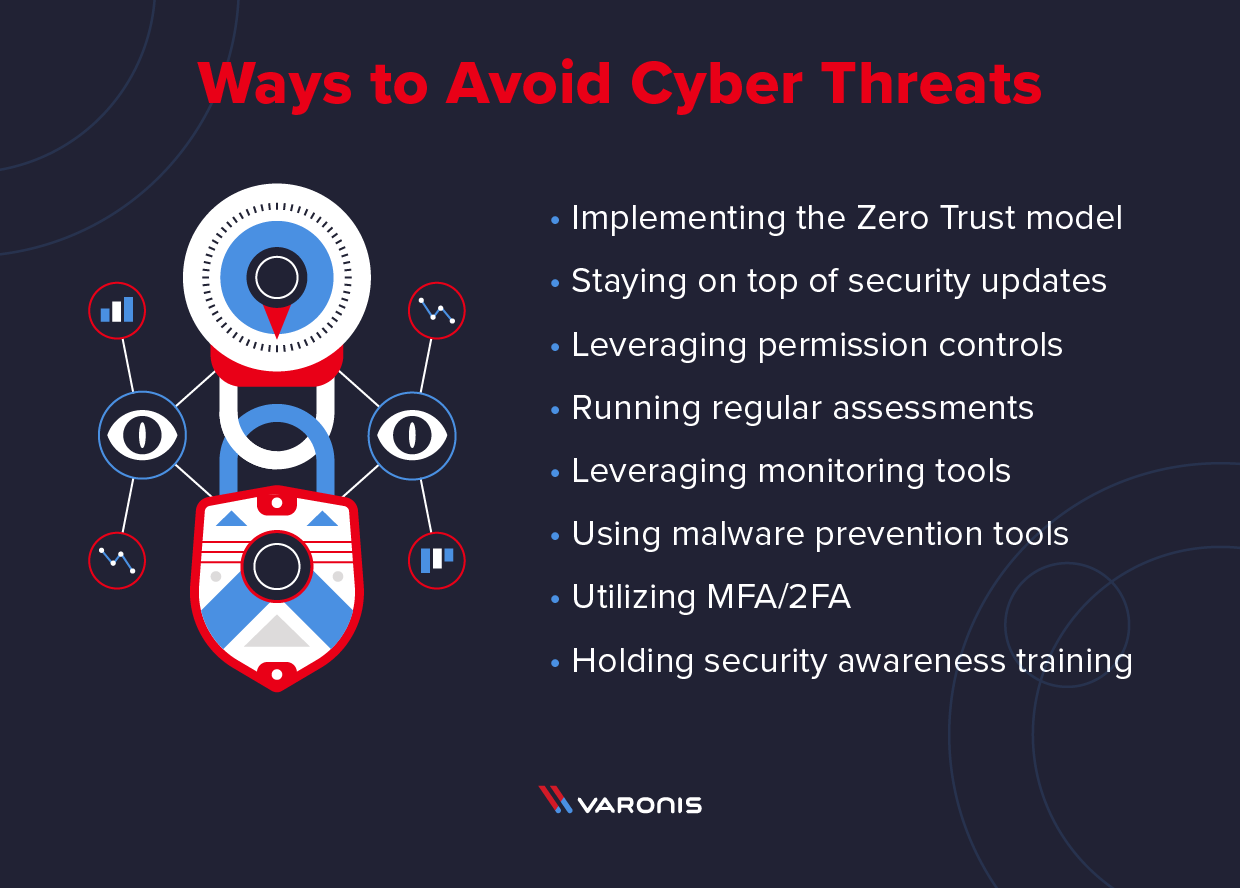
The solutions for cyber security threats are multifaceted and involve a combination of technological, procedural, and educational measures. To effectively mitigate these threats, organizations and individuals must adopt a comprehensive approach that includes implementing firewalls, intrusion detection systems, and encryption technologies to protect against hacking, malware, and phishing attacks. Additionally, regular software updates and vulnerability assessments are crucial to identify and address potential weaknesses in systems and applications.
Implementing Security Measures
Implementing security measures is a critical step in protecting against cyber security threats. This involves deploying security software and hardware to detect and prevent intrusions. Some key measures include:
- Installing anti-virus and anti-malware software to protect against viruses and malware.
- Implementing firewalls to control incoming and outgoing network traffic.
- Using encryption to protect sensitive data both in transit and at rest.
Developing Incident Response Plans
Developing incident response plans is essential for minimizing the impact of cyber security threats. These plans outline the steps to be taken in the event of a security breach and include procedures for containment, eradication, recovery, and post-incident activities. Key aspects of incident response plans include:
- Establishing an incident response team to manage the response efforts.
- Conducting regular drills and training exercises to ensure preparedness.
- Reviewing and updating the plan regularly to reflect changes in the threat landscape.
Enhancing User Awareness and Education
Enhancing user awareness and education is a vital component of cyber security. Educated users are less likely to fall victim to social engineering attacks and are more likely to follow best practices for password management, email safety, and safe browsing. Key educational initiatives include:
- Providing regular training sessions on cyber security awareness.
- Distributing guidelines and tips on safe computing practices.
- Conducting phishing simulations to test users’ ability to identify and report suspicious emails.
What is the best protection against digital or cyber attacks?

The best protection against digital or cyber attacks is a combination of technological measures, education, and best practices. This includes implementing firewalls, antivirus software, and encryption to prevent unauthorized access to computer systems and data. Additionally, individuals and organizations should use strong passwords, multi-factor authentication, and keep their software and operating systems up to date to prevent exploitation of known vulnerabilities.
Understanding Cyber Threats
To protect against cyber attacks, it is essential to understand the types of threats that exist. This includes malware, phishing, ransomware, and denial-of-service attacks. Individuals and organizations should be aware of the risks associated with using the internet and take steps to mitigate them. Some key measures to prevent cyber attacks include:
- Using reputable antivirus software to detect and remove malware
- Being cautious when opening email attachments and clicking on links from unknown sources
- Implementing firewalls and intrusion detection systems to prevent unauthorized access to computer systems
Best Practices for Cybersecurity
To protect against digital or cyber attacks, individuals and organizations should follow best practices for cybersecurity. This includes using strong passwords, enabling multi-factor authentication, and keeping software and operating systems up to date. Additionally, individuals and organizations should use encryption to protect sensitive data and implement incident response plans in case of a cyber attack. Some key measures to follow best practices for cybersecurity include:
- Using password managers to generate and store unique, complex passwords
- Implementing multi-factor authentication to add an extra layer of security to login processes
- Regularly backing up data to prevent losses in case of a cyber attack
Technological Measures for Cyber Protection
There are several technological measures that can be implemented to protect against digital or cyber attacks. This includes using firewalls, intrusion detection systems, and encryption to prevent unauthorized access to computer systems and data. Additionally, individuals and organizations can use virtual private networks (VPNs) to securely access the internet and secure sockets layer (SSL) certificates to encrypt data transmitted over the internet. Some key technological measures for cyber protection include:
- Implementing network segmentation to isolate sensitive data and systems
- Using artificial intelligence and machine learning to detect and respond to cyber threats
- Implementing security information and event management (SIEM) systems to monitor and analyze security-related data
What do businesses companies use cybersecurity to protect against?

Businesses and companies use cybersecurity to protect against various types of threats that can compromise their data, systems, and networks. These threats can come in many forms, including hacking, phishing, malware, and ransomware. The primary goal of cybersecurity is to prevent or minimize the impact of these threats, ensuring the confidentiality, integrity, and availability of business assets.
Types of Cyber Threats
Businesses face a range of cyber threats that can have significant consequences. Some of the most common types of threats include:
- Malware: Software designed to harm or exploit a computer system, such as viruses, Trojans, and spyware.
- Phishing: A type of social engineering attack that involves tricking employees into revealing sensitive information, such as login credentials or financial information.
- Denial of Service (DoS): A type of attack that aims to make a network or system unavailable by overwhelming it with traffic, making it impossible for legitimate users to access.
Cybersecurity Measures
To protect against cyber threats, businesses implement various cybersecurity measures. These measures include:
- Firewalls: Network security systems that monitor and control incoming and outgoing traffic based on predetermined security rules.
- Encryption: The process of converting plaintext data into unreadable ciphertext to protect it from unauthorized access.
- Access Control: Measures that restrict access to sensitive data and systems, such as passwords, biometric authentication, and role-based access control.
Importance of Cybersecurity
The importance of cybersecurity cannot be overstated, as the consequences of a cyber attack can be severe and long-lasting. Some of the key reasons why businesses prioritize cybersecurity include:
- Protection of Sensitive Data: Businesses handle large amounts of sensitive data, including customer information, financial data, and intellectual property.
- Prevention of Financial Loss: Cyber attacks can result in significant financial losses, including lost revenue, damage to reputation, and legal liabilities.
- Compliance with Regulations: Businesses must comply with various cybersecurity regulations and standards, such as GDPR and HIPAA, to avoid fines and penalties.
Frequently Asked Questions
What are the most common types of digital threats that businesses face today?
Businesses today face a wide range of digital threats, including malware, phishing, ransomware, and denial-of-service (DoS) attacks. These threats can come from various sources, including hackers, cybercriminals, and even insider threats. To protect against these threats, businesses need to implement robust cybersecurity measures, such as firewalls, intrusion detection systems, and encryption. Additionally, businesses should also focus on employee education and awareness, as human error is often the weakest link in the security chain. By understanding the types of threats they face and taking proactive steps to mitigate them, businesses can reduce the risk of a data breach or other cybersecurity incident.
How can businesses protect their sensitive data from unauthorized access?
To protect their sensitive data from unauthorized access, businesses should implement strong access controls, including multi-factor authentication and role-based access control. They should also use encryption to protect data both in transit and at rest, and ensure that all data backups are stored securely. Furthermore, businesses should conduct regular security audits and risk assessments to identify vulnerabilities and address them before they can be exploited. It is also essential to have an incident response plan in place, which outlines the steps to be taken in the event of a data breach or other cybersecurity incident. By taking these steps, businesses can ensure that their sensitive data is protected from unauthorized access and that they are compliant with relevant data protection regulations.
What are the benefits of implementing a cybersecurity solution for my business?
Implementing a cybersecurity solution can bring numerous benefits to a business, including protection of sensitive data, prevention of financial loss, and reduction of downtime. A cybersecurity solution can help to detect and respond to cyber threats in real-time, reducing the risk of a data breach or other cybersecurity incident. Additionally, a cybersecurity solution can help businesses to comply with regulatory requirements, such as GDPR and HIPAA, and demonstrate a commitment to data protection and cybersecurity. By investing in a cybersecurity solution, businesses can also enhance their reputation and build trust with their customers, partners, and stakeholders. Furthermore, a cybersecurity solution can help businesses to improve their overall security posture and reduce the risk of a cyber attack.
How can I ensure that my cybersecurity solution is effective and up-to-date?
To ensure that a cybersecurity solution is effective and up-to-date, businesses should regularly review and assess their security controls and incident response plan. They should also stay informed about the latest cyber threats and security trends, and update their security systems and software regularly. Additionally, businesses should conduct regular security testing and vulnerability assessments to identify weaknesses and address them before they can be exploited. It is also essential to have a incident response plan in place, which outlines the steps to be taken in the event of a data breach or other cybersecurity incident. By taking these steps, businesses can ensure that their cybersecurity solution is effective and up-to-date, and that they are protected against emerging threats. Furthermore, businesses should consider partnering with a cybersecurity expert or managed security service provider to help them stay ahead of the threats and ensure the effectiveness of their cybersecurity solution.

